Simple solutions for blocking malwares in Windows
I've been talking about manual malware removal in most of my blog, now we talk about prevention. As the saying goes, "a byte of prevention better than a megabyte of cure." This technique is not limited to blocking wscript.exe, which we will be discussing later, but to any application as long as you know the file name. I've been using this procedure way back in 2009 to remove any unknown malware.
For starters, we use what's built in with Windows (I'll discuss 3rd party apps later) using Group Po;icy Editor, some registry tweaks and using a small VBS file to terminate all running scripts a few seconds after Windows startup.
I. Group Policy Editor
- Launch gpedit.msc
- Go to User Configuration | Administrative Templates | System and double click on Don't run selected Windows applications
- Enable and click on Show... button
- Click Add...
- Type the filename of the application you want to block, wscript.exe in our example and click OK
- Wscript.exe is now added to our list. Click OK
- Click OK
- Exit gpedit.msc
Now let's test if our restriction works by running a vbs file.
That's is. Now you can easily remove any worm in your system by doing a full scan with an updated antivirus.
II. Registry Tweaks
Blocking program execution
This technique is similar to what gpedit.msc would do when you don't allow an application from executing. We will be using two registry scripts to accomplish this. One is for blocking and another for unblocking.Copy/paste the following and save it as Block.reg. Just like in How to block or prevent malware from running Part 1, we'll be using wscript.exe as our example.
Windows Registry Editor Version 5.00
; Block an application
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
"DisallowRun"=dword:00000001
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun]
"1"="wscript.exe"
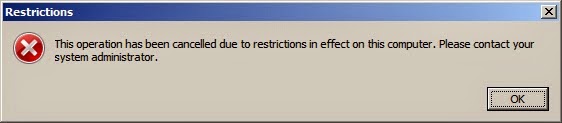 |
| Running a VBS File with restrictions |
When you're done with scanning and your system is already clean from infections, you can unblock wscript.exe by using the next registry script. Save the following as Unblock.reg.
Windows Registry Editor Version 5.00
; Unblock an application
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
"DisallowRun"=-
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun]
"1"=-
Note that this technique is not limited to VBS worms. I used this method for removing malwares like Daprosy worms, or any unknown trojan that can't be deleted easily because it's locked by a running process. Sometimes, only gpedit.msc, taskman, regedit and cmd are all you need to remove low to medium malware threats.
Making Notepad the default file handler for VBS files
Another way to prevent VBS worms from running is to use Notepad instead of WScript as VBE and VBS files default file handler. This way the worm would open in Notepad instead of executing making it easier to remove.Copy/paste the following and save it as "Open VBE VBS with Notepad.reg"
Windows Registry Editor Version 5.00
;Open VBE/VBS file with Notepad by WinXPert
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VBEFile\Shell\Open\Command]
@=hex(2):22,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,4e,00,\
6f,00,74,00,65,00,70,00,61,00,64,00,2e,00,65,00,78,00,65,00,22,00,20,00,25,\
00,31,00,00,00
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VBSFile\Shell\Open\Command]
@=hex(2):22,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,4e,00,\
6f,00,74,00,65,00,70,00,61,00,64,00,2e,00,65,00,78,00,65,00,22,00,20,00,25,\
00,31,00,00,00
 |
| Opening a VBS File with Open VBE VBS with Notepad.reg merged to registry. |
And here is the companion script to revert VBE/VBS handling back to it's default settings. Save this one as "Open VBE VBS with WScript (Default).reg"
Windows Registry Editor Version 5.00
;Open VBE/VBS file with WScript.exe (default)
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VBEFile\Shell\Open\Command]
@=hex(2):22,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,57,00,\
53,00,63,00,72,00,69,00,70,00,74,00,2e,00,65,00,78,00,65,00,22,00,20,00,22,\
00,25,00,31,00,22,00,20,00,25,00,2a,00,00,00
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VBSFile\Shell\Open\Command]
@=hex(2):22,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,57,00,\
53,00,63,00,72,00,69,00,70,00,74,00,2e,00,65,00,78,00,65,00,22,00,20,00,22,\
00,25,00,31,00,22,00,20,00,25,00,2a,00,00,00
 |
| Running a VBS File with default file handler |
III. Killing wscript process at every Windows startup
What we'll do
here is to add a small batch file or a vbs file at Windows Startup
folder. What these utilities would do is to terminate any wscript
processes that started with Windows after a 10 second delay. If
none is detected, it will ternimate itself and not remain in running
memory. This is a sort of set it and forget it option. Not the most elegant of codes but it works. If a wscript process is detected and terminated, you can easily do a full scan with an updated antivirus.
For this script, I'll use Batch Enhancer (BE.EXE) from NDOS 6,0, yup from the good old DOS days. Copy BE.EXE to your Windows folder. It will provide us with a 10 second delay. You can also use NIRCMD to get the job done.
Copy/paste the following and save it as VBS Killer.bat or VBS Killer.cmd.
@ECHO OFF
COLOR 17
CLS
TITLE - VBS WORM KILLER
ECHO VBS WORM KILLER
ECHO.
BE DELAY 180
TASKLIST.EXE > "%TEMP%\IT.LOG"
FIND /I "WSCRIPT.EXE" "%TEMP%\IT.LOG" >NUL
IF NOT ERRORLEVEL 1 (
ECHO WSCRIPT.EXE Detected. Terminating process...
TASKKILL.EXE /F /IM "WSCRIPT.EXE"
ECHO.
ECHO A VBS worm was detected running in your system. Scan your PC.
ECHO.
START www.winxpert3.blogspot.com
PAUSE
)
Create a shortcut of this file to your Windows Startup folder.
Note: You can also use this batch file to kill a VBS worm in case you inadvertently got infected again while working with your USB Flash drives.
To be continued...
Please visit my blog on manual malware removal
All my tutorials are based on my own research. If you find this tutorial useful, please comment or share. You can also help fund my continued work by making a donation. Thank you and GOD bless!
To GOD be the glory!
All content ("Information") contained in this report is the copyrighted work of WinXPert: Virus and Malware Removal.
The Information is provided on an "as is" basis. WinXPert disclaims all warranties, whether express or implied, to the maximum extent permitted by law, including the implied warranties that the Information is merchantable, of satisfactory quality, accurate, fit for a particular purpose or need, or non-infringing, unless such implied warranties are legally incapable of exclusion. Further, WinXPert does not warrant or make any representations regarding the use or the results of the use of the Information in terms of their correctness, accuracy, reliability, or otherwise.
Copyright © 2015 WinXPert. All rights reserved. All other trademarks are the sole property of their respective owners.









No comments:
Post a Comment